I don’t post (or even tweet) very much about the malware going through my sandbox; in most cases it has been blogged about by more than one person in way more depth than I could. The other day, however, one stood out in my feed for a few reasons –
- it was the first time I’d had a Remcos sample
- contrary to what most blogs I read about it said, its C2 traffic was in the clear
- despite knowing that Emerging Threats had multiple signatures explicitly for Remcos, I didn’t see any of them fire
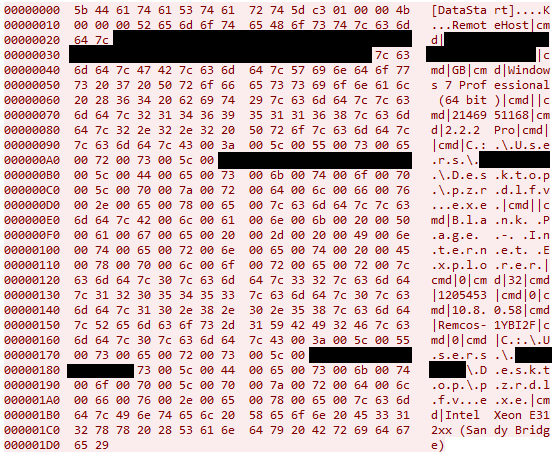
The content is exactly what one would expect – an array of values holding parameters of the infected host, separated by the string “|cmd|”, but no decryption was necessary.
Someone familiar with Remcos might also have spotted another odd feature from the above screenshot; the value “10.8.0.58” is the address of its C2 server. Given that my sandbox doesn’t have any route to a device with that address, these connections inevitably failed.
What is the point of having a private IP as a C2 server? Two possibilities spring to mind:
- The sample was intended for a target network with an established foothold serving as an internal C2
- It is an unfinished or test sample and the address is for the creator’s lab C2 server
I lean strongly toward the latter, given who it was sent to and that the data was also unencrypted, though I’m open to other ideas.
SHA256:
65f79343dea4024d439ef00d9effa663c76e2d683d49a7327f64aef673efb9d3